
It is well known now by both the cyber and non cyber community that one of the major problems in the world today concerning the internet is the issue of computer hacking possessing new breaches of data and releases of ransomware occurring at a fast rising rate. Computer hacking was once the realm of curious teenagers. It’s now the arena of government spies, professional thieves and soldiers of fortune. Cyber criminals have showed times without number that they know no limit and boundary, they have committed cyber crimes from a low level of individual to a level of some world’s largest corporations, and they even show no sign of slowing down. Even more, cyber security solutions that are proactive in discovering new threats and allowing end users to shut them out or close them down are in minimal and low supply. Eliminating cyber security threats requires more than antivirus protection, firewalls and intrusion detection systems and that is why UNCLOAK is being introduced;
UNCLOAK is a unique and fully scalable blockchain technology that provides businesses the advantage to monitor, protect themselves from cyber threats and also eliminate them. It is an analytical tool based on artificial intelligence for the intuitive, automated and seamless performance of security checks, providing users the ability to scale through the cyber insecurities and understand, in the process resolving cyber security issues.
UNCLOAK aims to build its own database by that detects threats by using advanced Artificial Intelligence (AI) technology to scan through both the public and private internet in search of the latest cyber threats, which are then converted into security signatures in process adding them to the Uncloak threat detection system to check if the vulnerabilities exist across the subscribed user base networks and infrastructure. The end user then gets the notification immediately so that corrective action can be taken immediately.
BUSINESS GOALS OF THE PLATFORM
- Vulnerabilities are not allowed to be added to the platform without approval from a pool of verified hunters chosen at random.
- End to end visibility of vulnerabilities found and payments to hunters within the Uncloak platform occur automatically without intervention.
- Real-time analytics and automated reporting with a locked audit trail of everything.
- Tamper-proof vulnerability database.
- Securely sharing data with all parties.
- Reduce reporting process time and effort for vulnerability checks
- Leaderboard system for all registered hunters/validators with bonus stars given to the most frequent contributors resulting higher in token payouts
USE CASES FOR UNCLOAK PLATFORM
=>SMALL CLIENTS(1-250 EMPLOYEES)
The platform is designed for companies and organisations that wish to perform their own security checks without requiring immediate attention from a certified ethical hacker or security penetration tester. It also performs a host of functions that a professional ethical hacker performs at greatly reduced cost to the company, from the listed below:
- Check Operating System and application software patch levels are up to date.
- Check for presence of l applications or software services with weak configurations and provide suggestions for improving the security of applications and hardware.
- Perform full vulnerability check of all workstations/servers/network hardware/software on an automated schedule basis without requirement for penetration tester/ethical hackers.
=>LARGE CLIENTS (250+ EMPLOYEES)
Uncloak software will elevate a number of compliance/certification concerns since large companies have a differing set of needs that are heavily compliance and IT governance related and Cyber Essentials certification place a continuous burden on IT teams also providing the following:
- Check for presence of vulnerable OS/network available applications /services /vulnerable transport layer encryption.
- Relevant reporting on upcoming cyber threats and IT security compliance benchmarks.
- Check for unneeded applications / services available on workstations/servers.
ECOSYSTEM & PARTNER GROUP
Uncloak intends to create a formal framework for how software development partners who wish to facilitate technology integration and to develop and promote enhanced product solutions can be supported in order to expand the breadth and capability across Uncloak as a global Cyber security solution. The platform aims to provide an interface for leading software development teams to implement our solution into their platforms that would allow end users to quickly power up the project in their private/ public cloud environment to the benefit of all parties involved:
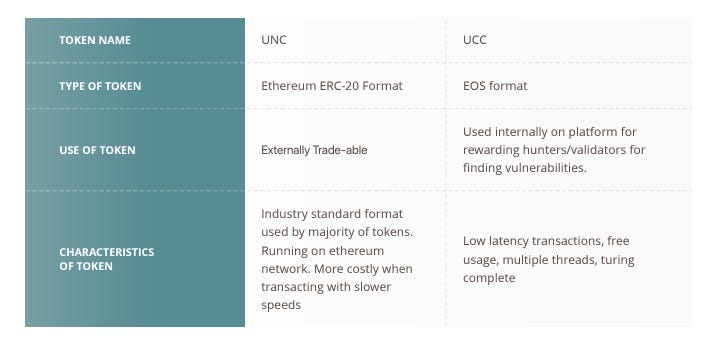
UNCLOAK TOKEN
Uncloak uses two tokens to power the platform.
- UNC tokens can be purchased on a token/crypto exchange using ethereum, neo, BTC dependent on the exchange used.
- UNC tokens purchased on an exchange can be used to purchase and subscribe to Uncloak platform along with fiat currency for subscription services.
- Hunters and validators who have earned UCC tokens on the Uncloak platform for either finding/ validating new vulnerabilities can convert tokens into tradable UNC tokens, which are then sent securely to the hunters/validators registered Crypto wallet.
- In the unlikely event that UCC tokens absorb the remaining amount of UNC tokens available an allocation of UCC tokens will be able to be exchanged for payments in Ethereum via the Uncloak platform.
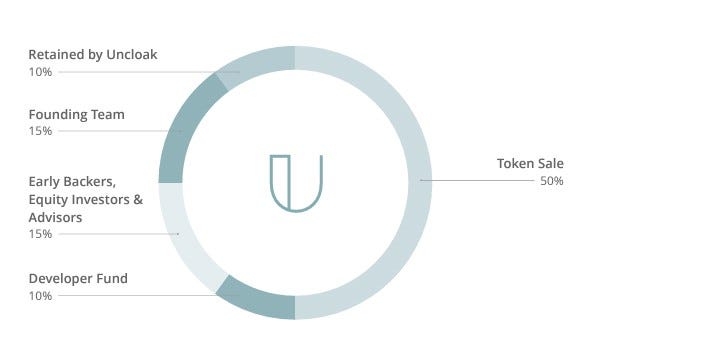
TOKEN SALE
Uncloak will be executing a token sale to raise funds for development and commercialisation of its next generation of cyber threat management. The maximum amount we will accept is a value of $21,000,000 USD. The only accepted currency will be ETH. Exact pricing of ETH to UNC will be determined at a later date prior to the official token sale.
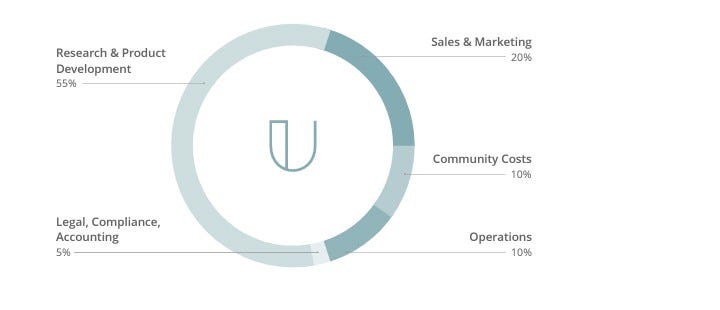
USE OF FUNDS
The platform use of funds is depicted below;
Let us seize this opportunity to study the project and understand its promising abilities in tackling and eliminating cyber insecurities.
For more information, kindly visit:
Website: https://uncloak.io
Whitepaper: https://whitepaper.uncloak.io
Twitter: http://twitter.com/uncloakio
Facebook: https://www.facebook.com/uncloakio
Telegram: https://t.me/uncloakio
Medium: https://medium.com/@uncloak.io
Whitepaper: https://whitepaper.uncloak.io
Twitter: http://twitter.com/uncloakio
Facebook: https://www.facebook.com/uncloakio
Telegram: https://t.me/uncloakio
Medium: https://medium.com/@uncloak.io
Author: teepheh
Author bitcointalk: https://bitcointalk.org/index.php?action=profile;u=2142272
No comments:
Post a Comment